Services
We provide comprehensive technical analysis and project guidelines to ensure precise network design and implementation. Our team consolidates all available data to ensure accurate specifications for each project.
Networking Support Services
Our experts install and configure networking equipment such as switches, routers, and wireless access points. We ensure that your hardware and software are correctly set up for optimal performance.
Hardware
Installation
We handle the entire process of hardware installation, from initial setup to full operational status. Our services are tailored to meet client-specific needs, ensuring smooth and efficient operation.
Equipment Training
We offer thorough training sessions to help users operate and maintain their equipment effectively. This ensures that our clients can manage and use their systems with confidence.

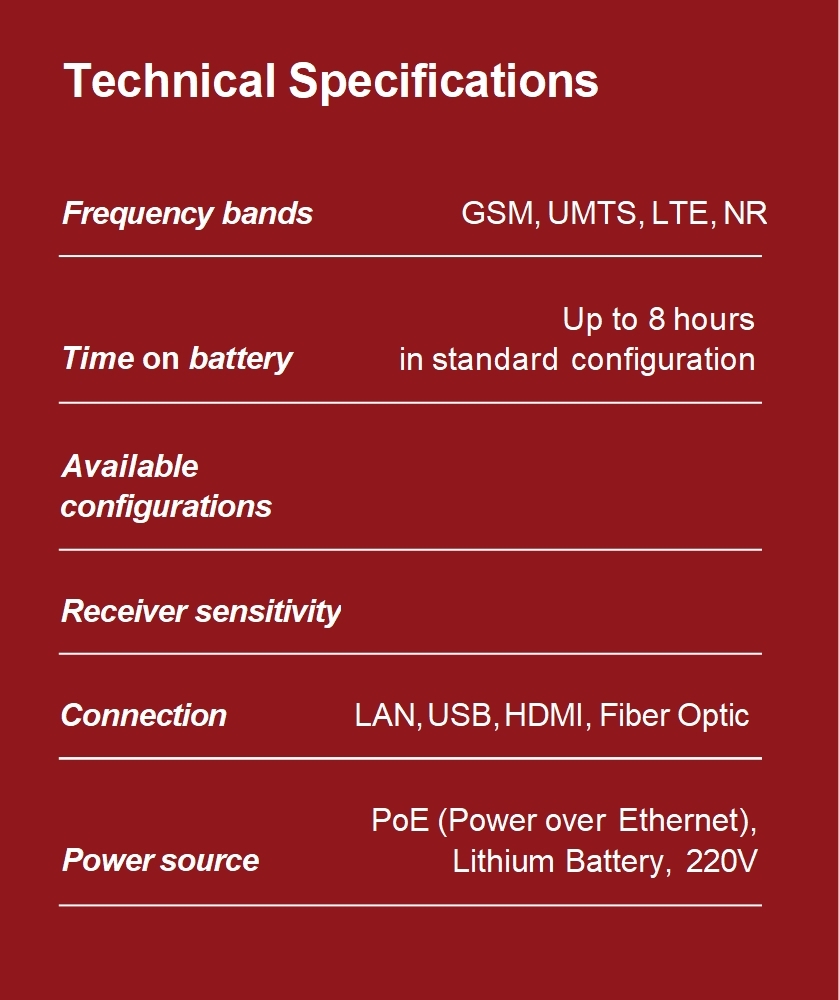
RB-CS1 CELLSHIELD
RB-CS1 CellShield perimeter security system is designed to safeguard and protect critical infrastructure from pervasive cellular network threats such as cell-site simulators, IMSI catchers, rogue base stations,
and unauthorized surveillance. CellShield is a versatile solution suitable for portable, stationary and distributed applications. designed to swiftly detect and disrupt the illegal surveillance
Applications: Case Study
VIP Protection
Portable units are used by Government Security services while accompanying the Prime Minister for his official duties, offering convenient transportation and on-the-go usage, significantly increasing officers’ situational awareness and allowing them to instantly identify and fight threatsTactical Team Support
A special force officer is tasked with obtatining information from a known target using an IMSI Catcher. Whatever he does, he is unable to catch the target’s phone because he is located right underneath a cell tower. Instead of requesting the provider to disable the cell down. he quickly utilizes CellShield to temporarily shut down the tower and instantly gets the target phone on the catcherFraud investigation
A network provider together with the designated authority use CellShield for detection of fake cells that were used by an organized scam network impersonating government officials and bank workersRB-CS1 CELLSHIELD
Real Time monitoring
2G / 3G / 4G / SG-NSA /SG SA
Rapid response
Threat disruption
Mapping with GPS positioning
User-friendly application with versatile control options
Unattended protection around the clock
Drone detection
Modes of Operation
Scanning
CellShield continuously monitors the network environment, utilizing all available channels to comprehensively assess the surroundings
Identification
Upon spotting a suspicious cell tower, CellShield allocates channels to disturb its function while retaining some for monitoring. Use visual and audible alerts for continuous awareness of unfavorable signals
Disruption
CellShield exhausts all available cell tower resources causing denial-of-service; Corrupt target’s dataset by flooding it with fake IMSI / IMEI identities
Application
01 VIP SECURITY
02 CRITICAL INFRASTRUCTURE SECURITY
03 FRAUD
04 SPECIAL OPERATIONS